Microsoft Multi-Factor Authentication
Starting in the Spring 2022 semester, PNW is implementing Microsoft’s multi-factor authentication (MFA) process to help protect University email and your personal information from security risks.
What is Multi-Factor Authentication (MFA)?
Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identification, such as entering a code on their cell phone or providing a fingerprint scan.
If you only use a password to authenticate a user, it leaves an insecure vector for attack. If the password is weak or has been exposed elsewhere, is it really the user signing in with the username and password, or is it an attacker? When you require a second form of authentication, security is increased as this additional factor isn’t something that’s easy for an attacker to obtain or duplicate.
How to configure Multi-Factor Authentication
You will be prompted to set up MFA when logging into your account after February 19th.
- Sign in to your account with your password like you normally do. After you choose Sign in, you’ll be prompted for more information.
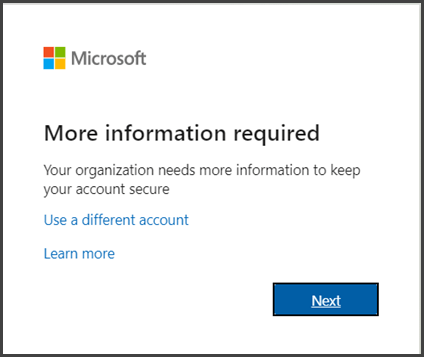
- Choose Next.
- The default authentication method is to use the free Microsoft Authenticator app. If you have it installed on your mobile device, select Next and follow the prompts to add this account. If you don’t have it installed there is a link provided to download it.If you would rather use SMS messages sent to your phone instead, select I want to set up a different method. Microsoft 365 will ask for your mobile number, then send you an SMS message containing a 6-digit code to verify your device.
Tip: For a faster, and more secure, experience we recommend using an authenticator app rather than SMS verification. - Once you complete the instructions to specify your additional verification method, the next time you sign in to Microsoft 365, you’ll be prompted to provide the additional verification information or action, such as typing the verification code provided by your authenticator app or sent to you by text message.
Note: Generally you’ll only need the additional verification method the first time you sign into a new app or device, or after you’ve changed your password. You will likely need to complete this verification on a regular basis, although not daily.
If you need additional instructions, they can be found in this video.
MFA Frequently Asked Questions
Setting up MFA
Microsoft MFA is currently being implemented at the West Lafayette campus. PNW will see its implementation during mid-February 2022.
Microsoft multi-factor authentication allows users to verify authentication using three methods: the Microsoft Authenticator App, SMS text messaging, or an audio phone call.
Users without a smartphone should follow the instructions in the video above, but instead of selecting “Authenticator App” they should select “phone.” Users will then be prompted to choose if they want to receive an authentication code via text message or a phone call. Follow the prompts provided by Microsoft to complete the enrollment processes.
Depending on your phone and email client, Microsoft MFA may not work with your smartphone’s email application.
In some cases, already established mail profiles can’t make the transition to MFA from single factor authentication and users should remove the email from your mail client on your phone, then re-add it to enable MFA security.
Microsoft’s Outlook App is a proven option that works with MFA; you can learn more about the Outlook App here.
Current Applications that are protected by MFA:
- Outlook (University email)
- Teams
- OneDrive
- Office 365 applications
- Microsoft Authenticator app (Preferred Method)
- Microsoft authenticator is the preferred solution for approving MFA requests. It provides simple push notifications so the user does not have to enter codes into the authentication dialogue, and can generate 6 digit codes if needed
- SMS Codes
- Users can receive text messages / SMS containing codes they an enter to approve the authentication.
- Phone Calls
- Users can register a cell or landline phone number to receive a call that prompts them to approve the authentication.
You can update your authentication methods by going to https://mysignins.microsoft.com/security-info.
Contact the PNW Customer Service Center at csc@pnw.edu or 219-989-2888.
General Information about MFA
Purdue Login is a separate two-factor authentication system for many of the University’s tools and services. Microsoft MFA is meant to protect email and other services provided by Microsoft.
PNW will require users to log in using their MFA credentials once every 90 days. Users who sign out of their Microsoft account, clear their browser cache, or log in from a new device will also be prompted to use MFA when signing in again.
ITaP is working with the Purdue University Retirees Association to implement multi-factor authentication for retiree accounts; additional information will be announced soon. However, retirees may also sign up now following the instructions listed above.
Multi-factor authentication means that anyone logging into your email account must know both the password and have something with them – like a cell phone or access to your landline telephone number.
If your account becomes compromised – say because of phishing or someone stealing your password – they still won’t be able to access your account because they are unable to provide the second required authentication factor.
To learn more, visit this page from Microsoft which explains more fully how MFA works.
No, but it should greatly reduce them.
Most phishing emails and other email-based scams sent to Purdue accounts are caught by spam filters. Occasionally, however, a phishing attack is successful, and the scammer gains access to a compromised account and uses it to send out additional emails to users within the Purdue system. Once 100 percent of our students, staff, and faculty have MFA, there will be very low likelihood of any additional compromised accounts thus drastically reducing successful phishing campaigns. However all email users should continue to be wary and follow the phishing advice found here.